Managed Cyber Security Solutions for UK Businesses
Cyber threats are becoming more advanced — and they can strike when you least expect it. Whether you’re a small business or a growing organisation, protecting your data and systems is essential. A single breach can cause financial loss, reputational damage, and major disruption.
At Mother, we make cybersecurity simple. Our expert team delivers tailored IT security solutions, from real-time threat monitoring to AI-powered detection, keeping your business secure and your operations running smoothly.
We don’t just react to threats — we anticipate and prevent them. Trust us to protect your business, so you can focus on what matters most.
Cybersecurity challenges are constantly changing — but protecting your business doesn’t have to be complicated. Our smart solutions help you stay secure, proactive, and resilient.
Empower your team with email filtering, real-time alerts, and hands-on training.
With multi-layered protection and rapid recovery, your data stays safe and accessible.
We monitor and adapt in real time to stop new threats before they impact your systems.
Secure every device, anywhere — with full visibility across your remote workforce.
Why juggle multiple tools and vendors? RoundClock wraps all 8 essential cybersecurity protections into one seamless solution — from threat detection and data protection to employee training and recovery. One solution. Total peace of mind.
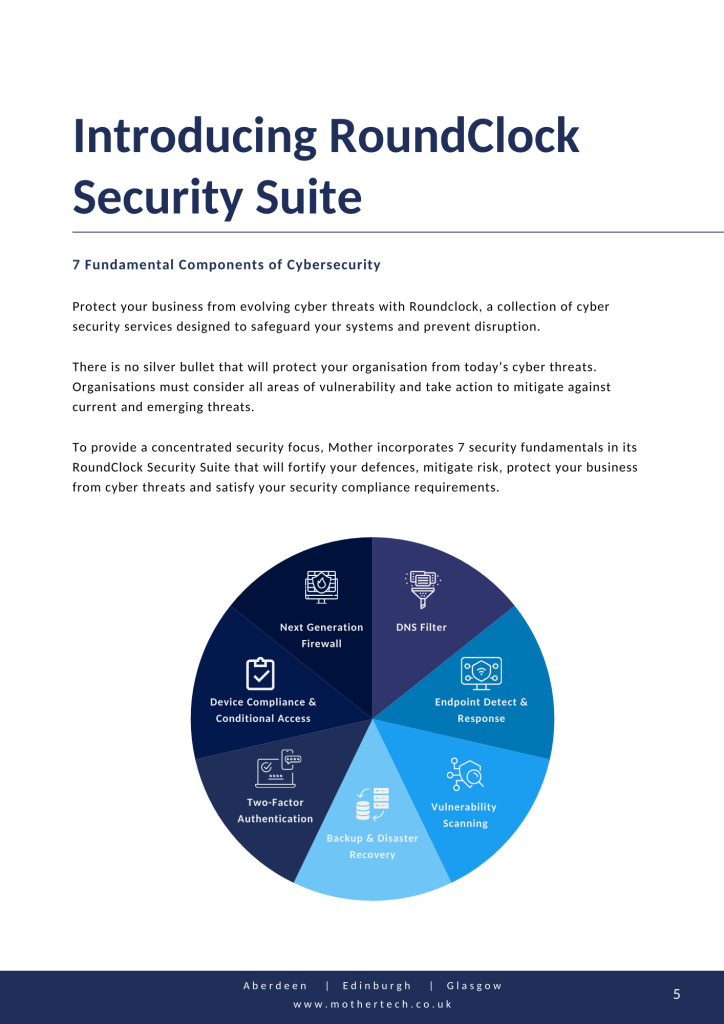
A DNS filter blocks access to malicious websites and provides off-site protection, helping businesses prevent cyber threats and secure remote workers.
→
Standard anti-virus falls short against advanced threats. RoundClock EDR uses AI to monitor devices and detect threats in real-time, continuously analysing data to identify potential cyberattacks.
→
Reliable backups are crucial as disasters and malware attacks pose significant threats, and cloud storage alone doesn’t guarantee protection.
→
Regular vulnerability scanning is crucial for cybersecurity. RoundClock offers thorough scanning services with detailed reports and recommendations to prevent exploitation and safeguard your business.
→
2FA adds extra security, making it harder for cybercriminals to access sensitive data and systems, and is essential in today’s digital environment despite initial reluctance.
→
Next Generation Firewalls (NGFW) surpass traditional firewalls by using in-depth traffic analysis to defend against modern cyberattacks, essential for protecting businesses from evolving threats.
→
Enforce device compliance and conditional access policies to manage risks, granting access only to devices that meet security criteria like up-to-date OS, active EDR, and DNS filters.
→
Cybercriminals target your staff as the easiest entry point through phishing, fake invoices, or spoofed messages. Firewalls can’t stop a bad click, so employee cyber awareness is no longer optional.
→

Our RoundClock Cybersecurity Brochure outlines all the essential elements of our comprehensive cybersecurity suite.
We continuously monitor your systems around the clock to detect and respond to threats in real time, minimising risk and downtime.
We deliver customised cybersecurity strategies tailored to your organisation's specific risks and regulatory needs.
With offices in Aberdeen, Edinburgh, and Glasgow, we provide robust cybersecurity support to businesses throughout Scotland.
Our professionals hold top industry certifications, giving you confidence that your cybersecurity is handled by trusted experts.
